This is a bit sinister: the China Internet Network Information Center (CNNIC) has been dropping digital certificates into the computers of everyone in China, which could potentially allow them to snoop on your normally secure ‘https’ web-surfing, such as your online banking and email.
CNNIC’s digital certificate, which is probably in your computer right now, has not been proved to be maliciously spying, but it’s a matter of trust. Do you really trust CNNIC, the overlords of the ‘Great Firewall’, to not be potentially peeking into your email, Facebook, Paypal account or online bank? Nope, thought not.
These digital certificates are not viruses or malware; they’re genuine tools that sites use to encrypt and verify information, and are issued by third-party Certificate Authorities (CA). For this CNNIC certificate to be on your computer, it has taken numerous levels of consent: by the web browser makers (Mozilla’s Firefox, Apple’s Safari, Google’s Chrome, Microsoft’s Internet Explorer, and more obscure ones, such as Opera) and by the CA ‘Entrust’, who will have evaluated, accepted and issued CNNIC’s digital certificate.
So, what’s the drama, you ask… Well, in devious hands, these important data snippets can be configured to pry, spy and snoop on your web traffic and private data. A benign digital certificate could turn malicious if remotely reconfigured, so as to tap into a certain users encrypted web data. In one other scenario, CNNIC could possibly use this tool in conjunction with the Great Firewall to tunnel into your encrypted web sessions. And, remember, CNNIC has a history of putting malware on people’s machines, hence all the alarm bells ringing over this tiny, new development.
So, let’s get about blocking CNNIC’s ass off of your computer: It’s best not to delete it – it’ll only be re-added – so we’re going to need to ‘never trust’ it in your computer’s settings. Then, you’ll be safe and unsnooped upon. It’s pretty easy, taking it step-by-step…
Mac: Safari and Chrome
This applies only to the Safari and Chrome web browser (Firefox needs to be done separately, in its own settings; see below). First, use Spotlight to search for the Keychain Access app (or, find it in Applications > Utilities folder) and launch it. Now, in the Keychain Access app search-box you should type CNNIC, and if their digital certificate is on your laptop, you will see 1 or 2 of them. If there’s nothing, that’s good. But, if you have 1 or 2 of the little buggers, this is what to do next: right-click on one of the digital certificates and select Get Info. A new window will appear; in this, click on the little arrow to the left of the word “Trust” so that more options are revealed. Now, in the first drop-down box you should select “Never trust” which’ll cause all the others drop-down boxes to also change to ‘Never trust’. Now that certificate is never, ever trusted, and will not be re-added since it already sits there. Repeat on the 2nd, if there is one.
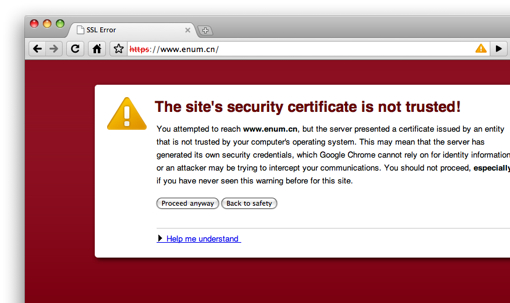
To check that it has worked, quit your browser(s), and then restart a browser and go to the website https://www.enum.cn where now a warning should appear saying that the site’s digital certificate is not trusted. If so, that’s great. If not (and the website loads normally), repeat the instructions more carefully.
Firefox (Windows, Mac, Linux)
First go to the Firefox ‘Preferences’ (on Mac), which is called ‘Options’ (I think) on Windows. Then, click the Advanced tab, then the Encryption tab, then click ‘View Certificates’. Next select the Authorities tab, and scroll down to find the CNNIC entry. Highlight the certificate, and then lower down click on the ‘Edit’ button, and in here you should now uncheck all the checkboxes, then click ‘Okay’. OK, that’s one blocked. Also scroll down to the Entrust.net entry, and see if there’s another CNNIC one in there. There’ll either be 1 or 2 in total. If there’s another one, repeat the above instrcutions.
To check that it has worked, quit Firefox, and then restart it and go to the website https://www.enum.cn where now a warning should appear saying that the site’s digital certificate is not trusted. If so, that’s great. If not (and the website loads normally), repeat the instructions more carefully.
Windows: Internet Explorer
I’m afraid I don’t have a clue how to do it on IE. And, seriously, with all the holes and bugs in IE, you should be thinking about ditching it for Firefox, pronto. But the Chinese blogger and techie Felix Yan, who first alerted me to this whole situation with his detailed blog post on the issue, has a step-by-step guide for Internet Explorer, though it’s all in Chinese, over on his site. Here’s the link for it.
Windows: Chrome
Google Chrome browser, for some reason, utilizes the digital certificates stored inside Internet Explorer, so you’ll also need to refer to Felix’s instructions for how to block CNNIC inside IE.







here’s some further reading on the whole issue, for those who want to get more into the technicalities of it:
* a plea to digi cert maker Entrust to not validate CNNIC: https://spreadsheets.google.com/viewform?formkey=dGctTVY0Y3VxX3lrXzZoeG90WDFBVXc6MA
* CNNIC’s previous malware: http://en.wikipedia.org/wiki/China_Internet_Network_Information_Center#Malware_Production_And_Distribution
* an overview of the CNNCI CA controversy, in English: http://www.wilderssecurity.com/showthread.php?p=1616924
* techies on Reddit discussing it: http://www.reddit.com/r/programming/comments/ax40m/cnnic_chinese_governments_organization_infamous/
* ‘Mozilla and CNNIC’ describes how Firefox came to accept the CNNIC digi cert: http://lwn.net/SubscriberLink/372386/d07c505fb87584ee/
in my system (os x snow leopard) i don’t get the red site as in the screen above. instead i just get an “are you sure you want to continue?” alert ad nauseum. which works just as well. just a heads up some people may get a different result for confirmation.
thanks for the tip steven.
Thanks for the tip.
Hey,
It’s not on every computer in China. Its a Root CA and it is supposed to be on every computer.
It doesn’t only affect internet traffic in China, It affect every connection Going through GFW bi-directional.
Imagine what a disaster this will be, if CNNIC repeat its .CN domain marketing policy with its shining new cert.
Just a reminder: the dot cn domain abuse has already amazed many security researchers.
I don’t see this on my computer. How do I block it if it’s not there?
@not chinese user – interesting to think that its on every single computer in the world, and therefore that it could potentially be eavesdropping on anyone who’s communicating with someone in China who’s behind the GFW. A lot of echoes of the Google hack/#GoogleCN issue in this, hence all the alarm and unease over this.
@Don – what web browser are you using?
I really don’t understand why laowai like you put up with living in a country you hate so much.
How does hating people spying and hacking our computers equate to hating China?
love China, hate the dictatorial party-state
Going by your “Firefox (Windows, Mac, Linux)” bit I see no separate CNNIC entry. I do see one under entrust.net. I am struggling to see why I should trust you, though. Seriously. Your author profile states “Steven has recently embraced the cathartic nature of blogging and twittering…” and in this post you seem to start from the premise of “OMG! It’s the Chinese government!”
I am restraining myself, really. I am not persuaded there is any greater a security risk than is embodied in any of the other apparently random shit that popped up when I followed your instructions.
Brilliant! Thanks for that Ryan. I will just add here the instructions for Explorer and Chrome (as explained in the CHinese blog you link):
– Go to Start Menu, click on “Run…”
– Type in certmgr.msc and OK.
– Open the folder “Untrusted Certificates”
– CLick Right on it and choose “all taks”. Choose “Import…”.
– Add the 3 CNIICC certificate files that you can find here:
http://felixcat.net/2010/01/throw-out-cnnic/
– Do the same for all your friends who are tech-phobic.
First time we score one to the GFW. Not sure how useful it will be, but it definitely feels good… Go FOS team!
Oops, I meant “thanks for that, Steven 🙂 ”
Clarification: the 3 certificates mentioned are the following files:
CNNICROOT.crt
CNNICSSL.crt
Entrust.netSecureServerCertificationAuthority.crt
Do some research on SSL and trusted certificate/untrusted certificate before you post!!
Hmmm.
Using Safari on a Mac. No certificate, and the web site you give (https://www.enum.cn) loads fine, with or without a vpn.
What’s with that?
I followed Uln’s comment for PC Chrome and went from getting:
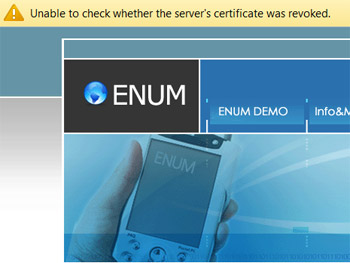
to getting:
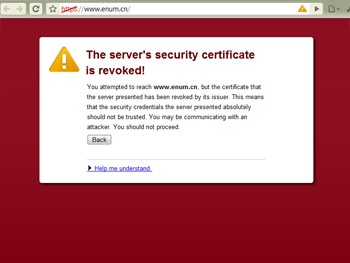
To clarify, I simply opened “certmgr.msc” and dragged the single CNNIC (CNNIC ROOT) certificate from “Trusted Root Certification Authorities\Certificates” to “Untrusted Certificates\Certificates”. For good measure I moved the Entrust.net certificates as well. I realize this may cause Security Error messages on other sites that Entrust.net has approved, but I’ll deal with that when the time comes.
Couldn’t find any certificates on the 3 computers in my home (1 mac, 2 pc’s), despite having been in China for years. I suppose this is a good thing? Surprised they didn’t exist on my computers.
Thanks to @Uln for adding advice for PC users on IE or Chrome. I’ll admit that I know little about encryption, certificates in general – as any expert will attest – but this seems worth doing, either as an ultra pre-cautious reinforcement of ones’ online liberties, or as a protest against CNNIC (who have a dubious track record in security and privacy) for a questionable move in creating this digital certificate.
Indeed, this whole CA/digi cert system is messed up. Why on earth do so many other companies – I see AOL and Deutsche Bank in my computer, too – have *any* kind of presence at all on our machines, when I never use their services (except for reading some AOL-owned blogs). Ah well… More important things in the world to deal with first…
Pingback: Most Tweeted Articles by Beijing Experts
Pingback: links for 2010-02-06 « dupola's Collections
@steven
though I wouldn’t trust the guys in ZNH a bit, this sounds scarier than it is, from what I understand.
They didn’t “drop” anything secretly as it sounds from you article, they applied at Mozilla and the guys at Mozilla said yes. They understand the technical part a bit better than most of us, so if there would have been big concern, I guess they would have said no.
And it would be very easy to detect it if CNNIC would issue wrong certificates. Espacially as they seem to be under close observation from mozialla themselves, after the outcry this caused.
So its certainly something to keep an eye on but nothing to worry to much about.
Anyway thanks for the pointer.
I don’t find any instructions on how to de-spy my computer. I’m using Firefox as a browser, but I have a PC. How do I do this?
Thanks,
Pelmo
I’m wrong. I mis-read the Mac/Windows part for Firefox.
OOPS…I followed the instructions below but it doesn’t go away.
Firefox (Windows, Mac, Linux)
First go to the Firefox ‘Preferences’ (on Mac), which is called ‘Options’ (I think) on Windows. Then, click the Advanced tab, then the Encryption tab, then click ‘View Certificates’. Next select the Authorities tab, and scroll down to find the CNNIC entry. Highlight the certificate, and then lower down click on the ‘Edit’ button, and in here you should now uncheck all the checkboxes, then click ‘Okay’. OK, that’s one blocked. Also scroll down to the Entrust.net entry, and see if there’s another CNNIC one in there. There’ll either be 1 or 2 in total. If there’s another one, repeat the above instrcutions.
To check that it has worked, quit Firefox, and then restart it and go to the website https://www.enum.cn where now a warning should appear saying that the site’s digital certificate is not trusted. If so, that’s great. If not (and the website loads normally), repeat the instructions more carefully.
This doesn’t make it go away. How 2?
OK, Geeks,
I got it to work. Thanks. K. T. Pelmo
I can’t find the CNNIC certificates but i disabled three Entrust.net certificates. I guess i’m safe for now.
Thanks for this
it works, that’s great! thank you !!
Woah. I’m in America and have trolled a bit on the People’s Daily site, etc. and I had one of those. That’s a little creepy, not going to lie.
Wow, I don’t know how I missed this post. Thanks, Ryan!
Oh and to Alfonso, we don’t hate China or we wouldn’t be here. We just hate Big Brother peering over our shoulder into our private lives and into our intimate space. When I was 8 I didn’t want my parents reading my personal journal, when I’m 34 I don’t want the Chinese government reading my personal thoughts either.
Steven,
I was referred to your post by the moderator of a Yahoo group I am on which deals with a lot of communication with China. I did find the CNNICROOT.crt and moved it from the trusted certificates to the untrusted certificates. I did not find the CNNICSSL.crt but did find the Entrust.netSecureServerCertificationAuthority.crt and moved that as well. I also found:
2 copies of Entrust.net Certification Authority (2048).crt
one copy of Entrust Root Certification Authority.crt
one copy of Entrust Root Certification Authority – G2.crt
I started to move these as well and then thought better of it since the names are slightly different. Should these 4 additional certificates be moved as well? Thanks.
I have various Entrust certificates also and had the same reservations about moving them to not trusted. Anybody?